Find hidden bugs in firmware, fast.
Autonomous binary pentesting.
No source code, no hardware, no test harnesses.
Backed by
You upload the binary.
Metalware finds the bugs.
Understand every vulnerability.
Every crash comes with an explanation, a stack trace, and a reproducible input. No reverse engineering required.
Root Cause Analysis
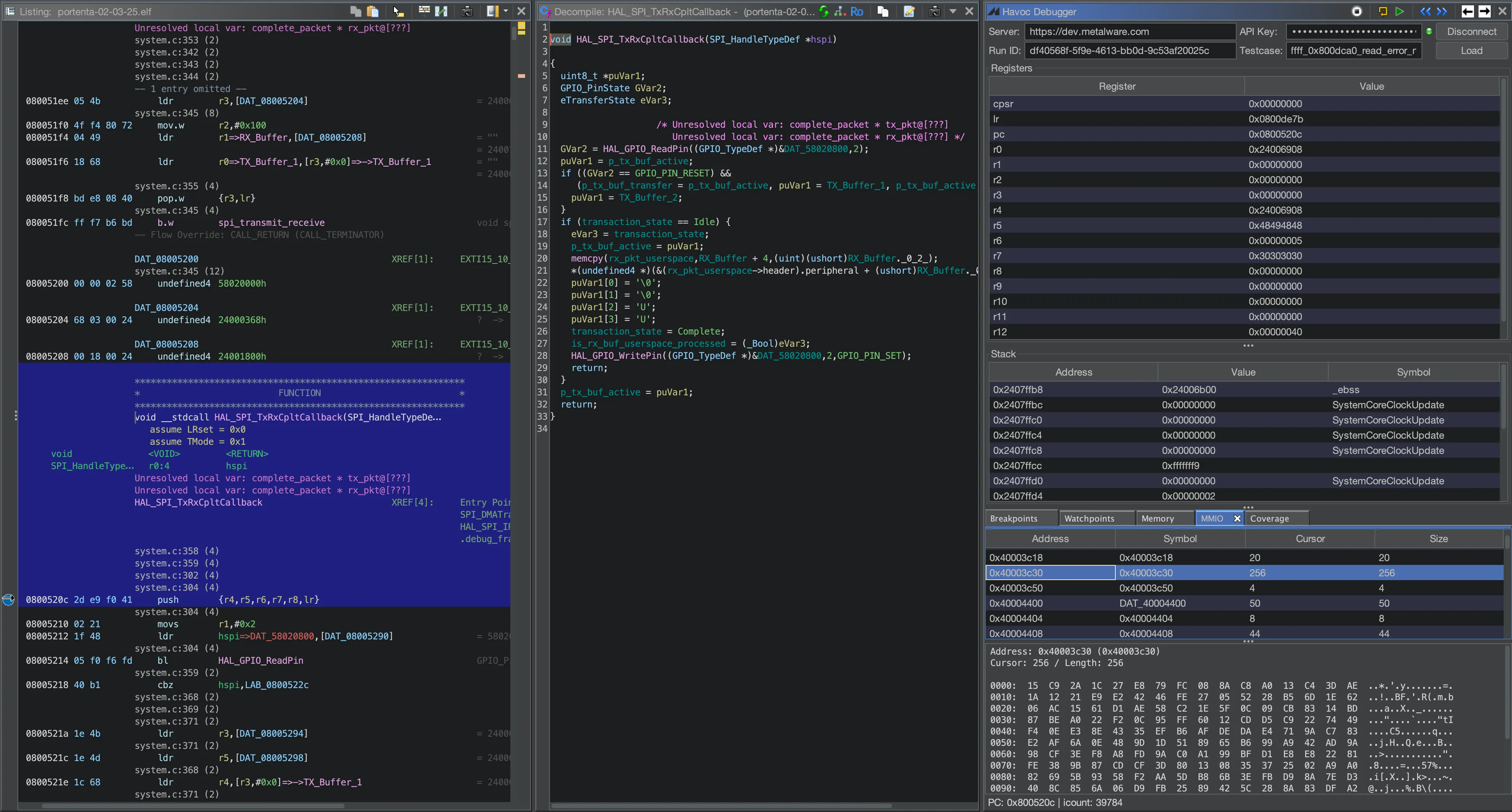
The crash is caused by a buffer overflow in HAL_SPI_TxRxCpltCallback. An
MMIO-derived 16-bit length value (0xc915 = 51477 bytes) read from the SPI FIFO data register
at 0x40003c30 is stored at address 0x24001800. This length is
subsequently used in a memcpy call that copies data to a destination buffer starting
at 0x24002000. The excessive length causes the copy to extend to 0x2400E915, overwriting adjacent memory including the SPI handle structure at 0x24006908.
The SPI handle's Instance pointer (first field at offset 0) is corrupted with zero.
void HAL_SPI_TxRxCpltCallback(...) { // 0x8005204
...
uint16_t len = *(uint16_t*)0x24001800; // len = 0xc915, MMIO-derived value from SPI FIFO
void *dst = *(void**)0x24000370; // dst = 0x24002000
void *src = 0x24001804;
memcpy(dst, src, len); // Overwrites SPI handle at 0x24006908
...
}
When HAL_SPI_Abort is later called, it reads the corrupted Instance pointer
(now NULL) from the SPI handle at 0x24006908 and attempts to dereference it at 0x800dca0, causing the null pointer access failure.
Stack Trace
0x0800fe26 LoopFillZerobss+0xc 0x080028bc main+0x2c 0x080051ee EXTI15_10_IRQHandler+0x1e 0x0800dca0 HAL_SPI_Abort+0x30
Debug with tools you know.
Replay any crash in GDB, Ghidra, or Binary Ninja.
Integrate into your pipeline.
Enhance your CI/CD with nightly fuzzing campaigns, short PR regression checks, automatic ticket filing and PDF reports.
Secure your firmware and supply chain.
Support industry requirements for robustness testing, vulnerability management, and Secure Software Development Lifecycle.
Automotive
ECUs, telematics, ADAS controllers, supply chain.
UNECE, ISO/SAE
Aerospace
Avionics, satellite systems, flight controllers.
DO-178C, DO-254, DO-326A
Medical
Infusion pumps, patient monitors, implantable devices.
FDA Cybersecurity Guidance
ICS & IoT
Protect your critical infrastructure.
EU CRA, IEC, NIST
Trusted by government and defense.
Metalware works with the United States and its allies to protect the hidden foundation of defense and critical infrastructure.
Fleetwide Assessment
Discover vulnerabilities at scale across device fleets and firmware repositories.
Supply Chain Analysis
Analyze firmware from third-party vendors and COTS components without source code.
Tailored Services
Leverage our expertise to address unique national security challenges.